Configuring Yandex Query
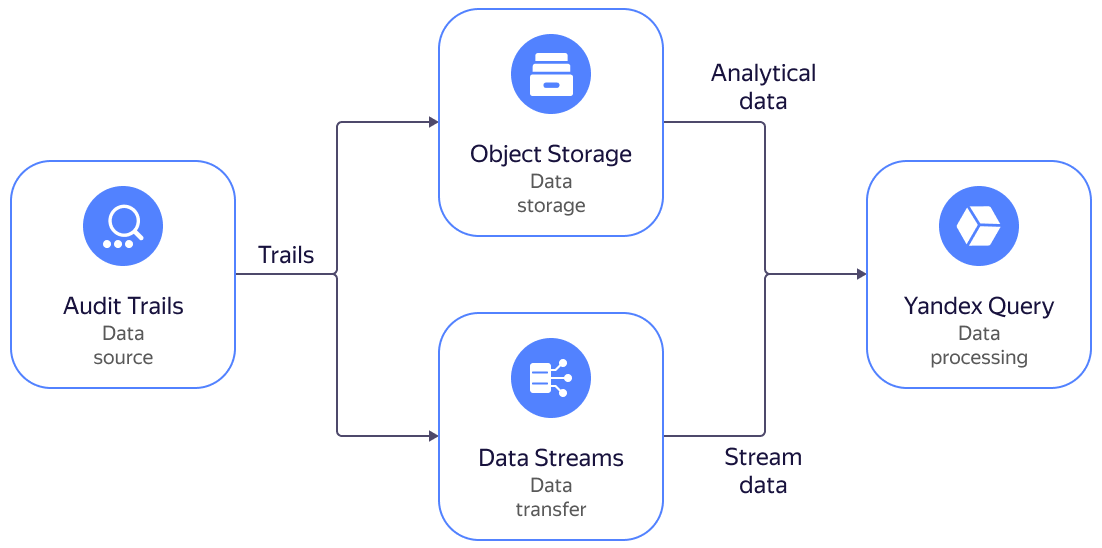
Yandex Query supports Audit Trails. You can analyze events of Yandex Cloud resources by running analytical and streaming YQL queries.
You can run analytical queries for logs stored in a bucket, and streaming queries for logs stored in Yandex Data Streams.
To connect a bucket with audit logs to Yandex Query and run YQL queries:
- Set up your environment.
- Create a connection between the trail and YQ.
- Run a query to logs in Object Storage.
If you no longer need the resources you created, delete them.
Getting started
Sign up for Yandex Cloud and create a billing account:
- Navigate to the management console
- On the Yandex Cloud Billing
ACTIVEorTRIAL_ACTIVEstatus. If you do not have a billing account, create one and link a cloud to it.
If you have an active billing account, you can navigate to the cloud page
Learn more about clouds and folders here.
If you do not have the Yandex Cloud CLI installed yet, install and initialize it.
Required paid resources
The cost of infrastructure support includes a bucket use fee (see Object Storage pricing).
Set up your environment
Create a bucket for audit logs
- In the management console
example-folder. - Select Object Storage.
- Click Create bucket.
- On the bucket creation page:
- Enter a name for the bucket according to the naming requirements.
- In the Read objects, Read object list, and Read settings fields, select
With authorization. - Leave other parameters at their defaults.
- Click Create bucket.
Create service accounts
Create a service account named trail-sa:
- In the management console
example-folder. - In the list of services, select Identity and Access Management.
- Click Create service account.
- Specify Name:
trail-sa. - Click Create.
Similarly, create a service account named bucket-yq-sa.
Assign permissions to service accounts
Assign the audit-trails.viewer and storage.uploader roles to the trail-sa service account:
-
The
audit-trails.viewerrole for your organization:yc organization-manager organization add-access-binding \ --role audit-trails.viewer \ --id <organization_ID> \ --service-account-id <service_account_ID>Where
--service-account-idis thetrail-saservice account ID.Result:
done (1s)For more information about the
yc organization-manager organization add-access-bindingcommand, see the CLI reference. -
The
storage.uploaderrole forexample-folder:yc resource-manager folder add-access-binding example-folder \ --role storage.uploader \ --subject serviceAccount:<service_account_ID>Where
--subjectis thetrail-saservice account ID.Result:
done (1s)For more information about the
yc resource-manager folder add-access-bindingcommand, see the CLI reference.
Assign the storage.viewer role for example-folder to the bucket-yq-sa service account:
yc resource-manager folder add-access-binding example-folder \
--role storage.viewer \
--subject serviceAccount:<service_account_ID>
Where --subject is the bucket-yq-sa service account ID.
Result:
done (1s)
For more information about the yc resource-manager folder add-access-binding command, see the CLI reference.
Create a trail
-
In the management console
example-folder. -
Select Audit Trails.
-
Click Create trail.
-
In the Name field, specify
logsyq. -
Under Destination, configure the destination object:
- Destination:
Object Storage. - Bucket: Select the bucket you created earlier.
- Destination:
-
Under Service account, select
trail-sa. -
Under Collecting management events, configure the collection of management event audit logs:
- Collecting events: Select
Enabled. - Resource: Select
Organization. - Organization: Automatically populated field containing the name of the current organization.
- Cloud: Keep the default value,
All.
- Collecting events: Select
-
Under Collecting data events, select
Disabledin the Collecting events field. -
Click Create.
Create a connection between the trail and YQ
You need to create a connection only when connecting the trail to YQ for the first time.
- In the management console
example-folder. - Select Audit Trails.
- Select the
logsyqtrail. - Click Process in YQ.
- Create a connection:
- Select the
bucket-yq-saService account. - Leave other parameters at their defaults.
- Select the
- Click Create.
- In the window with data binding options, click Create.
This will take you to the page for creating a query to trail logs.
Run a query to logs in Object Storage
Open the page to create an analytical query to Audit Trails logs:
- In the management console
- In the list of services, select Audit Trails.
- Select the trail for which you configured a connection to YQ.
- Click Process in YQ to go to the analytical query execution page.
Run event queries for the audit-trails-logsyq-object_storage binding:
-
Deleting a folder:
-
Select this query from the list: 1. Find out who deleted the folder.
-
Edit the query by specifying the folder ID:
SELECT * FROM bindings.`audit-trails-logsyq-object_storage` WHERE JSON_VALUE(data, "$.event_type") = 'yandex.cloud.audit.resourcemanager.DeleteFolder' and JSON_VALUE(data, "$.details.folder_name") = '<folder_ID>' LIMIT 100; -
Click Execute.
-
-
Enabling access via the serial console:
-
Select this query from the list: 6. Changing a VM: Adding serial console access.
-
Edit the query by specifying the number of displayed records:
SELECT * FROM bindings.`<audit-trails-logsyq-object_storage>` WHERE JSON_VALUE(data, "$.event_type") = 'yandex.cloud.audit.compute.UpdateInstance' and JSON_VALUE(data, "$.details.metadata_serial_port_enable") = '1' LIMIT <number_of_records>; -
Click Execute.
-
-
Changing access permissions for an Object Storage bucket:
-
Select this query from the list: 11. Suspicious activity with the Audit Trails log repository (Object Storage bucket).
-
Edit the query by specifying the number of displayed records:
SELECT * FROM bindings.`audit-trails-logsyq-object_storage` WHERE (JSON_VALUE(data, "$.event_type") = 'yandex.cloud.audit.storage.BucketAclUpdate' or JSON_VALUE(data, "$.event_type") = 'yandex.cloud.audit.storage.BucketPolicyUpdate') LIMIT <number_of_records>; -
Click Execute.
-
-
Assigning admin permissions:
-
Select this query from the list: 20. Assigning admin permissions (for a folder and cloud).
-
Edit the query by specifying the number of displayed records:
SELECT * FROM bindings.`audit-trails-logsyq-object_storage` WHERE JSON_VALUE(data, "$.details.access_binding_deltas.access_binding.role_id") = 'admin' LIMIT <number_of_records>; -
Click Execute.
-
How to delete the resources you created
If you created a separate bucket to complete this tutorial, you can delete it to stop paying a bucket use fee.