Connecting to a node over SSH
To connect to a Managed Service for Kubernetes cluster node over SSH:
-
Add the public key to the metadata when creating a Managed Service for Kubernetes node group.
Note
SSH connection using a login and password is disabled by default on Linux images that are used on Managed Service for Kubernetes nodes.
-
Configure security groups for the Managed Service for Kubernetes cluster.
Warning
Security group settings may block connection to the Managed Service for Kubernetes cluster.
For more information, see Connecting to a VM over SSH.
Individual nodes in node groups are Yandex Compute Cloud virtual machines with automatically generated names. To configure nodes, follow the steps below or other node group management guides.
Alert
Do not change node VM settings, including names, network interfaces, and SSH keys, using the Compute Cloud interfaces or SSH connections to the VM.
This can disrupt the operation of individual nodes, node groups, and the whole Managed Service for Kubernetes cluster.
Create SSH key pairs
Prepare the keys to use with your Managed Service for Kubernetes cluster node. To do this:
-
Open the terminal.
-
Use the
ssh-keygencommand to create a new key:ssh-keygen -t ed25519After running this command, the system will prompt you to specify the names of files to store the keys and enter the password for the private key. The default name is
id_ed25519. Keys are created in the~/.sshdirectory.The public part of the key will be saved to a file named
<key_name>.pub.
-
Run
cmd.exeorpowershell.exe. -
Use the
ssh-keygencommand to create a new key. Run this command:ssh-keygen -t ed25519After running this command, the system will prompt you to specify the names of files to store the keys and enter the password for the private key. The default name is
id_ed25519. Keys are created in theC:\Users\<username>\.ssh\directory.The public part of the key will be saved to a file named
<key_name>.pub.
Create keys using PuTTY:
-
Download
-
Add the folder with PuTTY to the
PATHvariable:- Click Start and type Change system environment variables in the Windows search bar.
- Click Environment Variables... at the bottom right.
- In the window that opens, find the
PATHparameter and click Edit. - Add your folder path to the list.
- Click OK.
-
Launch the PuTTYgen application.
-
Select Ed25519 as the pair type to generate. Click Generate and move the cursor in the field above it until the key is created.
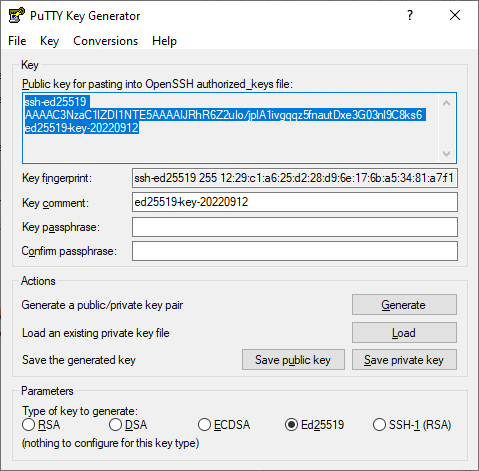
-
In Key passphrase, enter a strong password. Enter it again in the field below.
-
Click Save private key and save the private key. Do not share its key phrase with anyone.
-
Save the key in a text file in a single line. To do this, copy the public key from the text field and paste it to a text file named
id_ed25519.pub.
Convert the public key to the metadata format
Your username and public key are the credentials for connecting to the Managed Service for Kubernetes cluster nodes over SSH. These credentials are provided using metadata in a specific format.
The public key you created earlier has the following format:
<key_type> <public_key_body> <optional_comment>
Here is an example:
ssh-ed25519 AAAAB3NzaC***********lP1ww ed25519-key-20190412
Create a file with credentials for connecting over SSH in the following format:
<username>:<key_type> <public_key_body> <username>
Here is an example:
testuser:ssh-ed25519 AAAAB3NzaC***********lP1ww testuser
This format is suitable for creating and updating a Managed Service for Kubernetes node group using the CLI, Terraform, and API interfaces, and for updating a node group using the management console. When creating a node group, separate Login and SSH key fields are used in the management console.
You can provide credentials for multiple users in one file.
Here is an example:
testuser1:ssh-ed25519 AAAAB3NzaC***********lP1ww testuser1 testuser2:ssh-ed25519 ONEMOREkey***********avEHw testuser2
Create a node group and add the public key
- In the management console
- Select your Managed Service for Kubernetes cluster.
- In the left-hand panel, select Node manager.
- Click Create a node group.
- Set the node group parameters.
- Under Access, specify the credentials to access the Managed Service for Kubernetes node:
- In the Login field, enter the username.
- In the SSH key field, paste the contents of the public key file.
- Click Create.
Metadata with credentials for connecting over SSH is provided to the Managed Service for Kubernetes node group as key=value pairs.
Warning
The user-data VM metadata key is not supported for user data transmission. Use the ssh-keys key to provide parameters for SSH connections.
If you do not have the Yandex Cloud CLI installed yet, install and initialize it.
By default, the CLI uses the folder specified when creating the profile. To change the default folder, use the yc config set folder-id <folder_ID> command. You can also set a different folder for any specific command using the --folder-name or --folder-id parameter.
To create a Managed Service for Kubernetes node group and provide user credentials for connecting over SSH, run this command:
yc managed-kubernetes node-group create \
--name <node_group_name> \
--cluster-name <cluster_name> \
--fixed-size <number_of_nodes_in_group> \
--network-interface security-group-ids=[<list_of_security_groups>],subnets=<subnet_name>,ipv4-address=nat \
--metadata-from-file ssh-keys=<path_to_credentials_file>
Where --metadata-from-file is the parameter to provide metadata to the node group as key=value pairs. In ssh-keys, specify the path to the file with credentials for connecting over SSH.
Metadata with credentials for connecting over SSH is provided to the Managed Service for Kubernetes node group as key=value pairs.
Warning
The user-data VM metadata key is not supported for user data transmission. Use the ssh-keys key to provide parameters for SSH connections.
-
Create a Terraform configuration file describing the Managed Service for Kubernetes node group by following the steps described in Creating a node group.
-
In the node group description, set the
ssh-keysmetadata key value for theinstance_template.metadataparameter:resource "yandex_kubernetes_node_group" "<node_group_name>" { cluster_id = yandex_kubernetes_cluster.<cluster_name>.id ... instance_template { metadata = { "ssh-keys" = file("<path_to_credentials_file>") ... } ... } ... } -
Make sure the configuration files are correct.
-
In the command line, navigate to the directory that contains the current Terraform configuration files defining the infrastructure.
-
Run this command:
terraform validateTerraform will show any errors found in your configuration files.
-
-
Confirm updating the resources.
-
Run this command to view the planned changes:
terraform planIf you described the configuration correctly, the terminal will display a list of the resources to update and their parameters. This is a verification step that does not apply changes to your resources.
-
If everything looks correct, apply the changes:
-
Run this command:
terraform apply -
Confirm updating the resources.
-
Wait for the operation to complete.
-
Timeouts
The Terraform provider sets time limits for operations with Managed Service for Kubernetes cluster node groups:
- Creating and editing: 60 minutes.
- Deleting: 20 minutes.
Operations in excess of this time will be interrupted.
How do I modify these limits?
Add the
timeoutssection to the cluster node group description, e.g.:resource "yandex_kubernetes_node_group" "<node_group_name>" { ... timeouts { create = "1h30m" update = "1h30m" delete = "60m" } } -
For more information, see this Terraform provider guide.
Metadata with credentials for connecting over SSH is provided to the Managed Service for Kubernetes node group as key=value pairs.
Warning
The user-data VM metadata key is not supported for user data transmission. Use the ssh-keys key to provide parameters for SSH connections.
To provide multiple credentials for connecting over SSH, convert the contents of the credentials file to a single line and separate the credentials from each other with a sequence of special CRLF characters (\r\n). You cannot use multiline messages in an API request with a JSON body.
Example of converted credentials:
testuser1:ssh-ed25519 AAAAB3NzaC***********lP1ww testuser1\r\ntestuser2:ssh-ed25519 ONEMOREkey***********avEHw testuser2
Use the create REST API method for the NodeGroup resource or the NodeGroupService/Create gRPC API call.
Credentials for connecting over SSH are provided in the nodeTemplate.metadata parameter in ssh-keys.
For more information about creating a Managed Service for Kubernetes node group and parameters to provide, see Creating a node group.
Update node group keys
To change the credentials for connecting over SSH to a Managed Service for Kubernetes node group, update its metadata.
Warning
The credentials for connecting over SSH will be completely overwritten. You will not be able to connect to the Managed Service for Kubernetes cluster nodes using the old credentials.
Warning
After you change the metadata using the management consoleReconciling: all the group nodes will be recreated for the changes to take effect.
- In the management console
- Select your Managed Service for Kubernetes cluster.
- In the left-hand panel, select Node manager.
- On the Node group tab, select the node group in which you want to update the credentials.
- In the top panel, click
- Expand Metadata.
- Replace the current value of
ssh-keyswith the contents of the credentials file. - Click Save.
-
View the description of the CLI command for adding and updating the Managed Service for Kubernetes node group metadata:
yc managed-kubernetes node-group add-metadata --help -
Run this command:
yc managed-kubernetes node-group add-metadata \ --name <node_group_name> \ --metadata-from-file ssh-keys=<path_to_credentials_file>You can get the node group name with the list of node groups in the folder.
-
Open the Terraform configuration file describing the Managed Service for Kubernetes node group.
For more information about creating this file, see Creating a node group.
-
In the node group description, change the value of the
ssh-keysmetadata key for theinstance_template.metadataparameter:resource "yandex_kubernetes_node_group" "<node_group_name>" { cluster_id = yandex_kubernetes_cluster.<cluster_name>.id ... instance_template { metadata = { "ssh-keys" = file("<path_to_credentials_file>") ... } ... } ... } -
Make sure the configuration files are correct.
-
In the command line, navigate to the directory that contains the current Terraform configuration files defining the infrastructure.
-
Run this command:
terraform validateTerraform will show any errors found in your configuration files.
-
-
Confirm updating the resources.
-
Run this command to view the planned changes:
terraform planIf you described the configuration correctly, the terminal will display a list of the resources to update and their parameters. This is a verification step that does not apply changes to your resources.
-
If everything looks correct, apply the changes:
-
Run this command:
terraform apply -
Confirm updating the resources.
-
Wait for the operation to complete.
-
-
For more information, see this Terraform provider guide.
-
To provide multiple credentials for connecting over SSH, convert the contents of the credentials file to a single line and separate the credentials from each other with a sequence of special CRLF characters (
\r\n). You cannot use multiline messages in an API request with a JSON body.Example of converted credentials:
testuser1:ssh-ed25519 AAAAB3NzaC***********lP1ww testuser1\r\ntestuser2:ssh-ed25519 ONEMOREkey***********avEHw testuser2 -
Get all the existing metadata for the node group using the get REST API method for the NodeGroup resource, and provide the node group ID in the
nodeGroupIdrequest parameter.You can get the name of a node group with the list of node groups in the folder.
The metadata will be listed as
key=valuepairs in thenodeTemplate.metadatafield of the response. -
Use the update REST API method for the NodeGroup resource and provide the following in the request:
-
Node group ID in the
nodeGroupIdparameter. -
updateMaskparameter set tonodeTemplate.metadata.Warning
The API method will assign default values to all the parameters of the object you are modifying unless you explicitly provide them in your request. To avoid this, list the settings you want to change in the
updateMaskparameter as a single comma-separated string. -
nodeTemplate.metadataparameter listing all current node group metadata askey=valuepairs without any changes.For
ssh-keys, replace the current value with the line with credentials you created.Example of listing metadata in a parameter
-
Current metadata keys in a node group:
"nodeTemplate": { "metadata": { "ssh-keys": "<current_credentials_in_single_line>", "<current_key_1>": "<current_value_1>", "<current_key_2>": "<current_value_2>" }, ... } -
Metadata keys to provide in an API request:
"nodeTemplate": { "metadata": { "ssh-keys": "<new_credentials_in_single_line>", "<current_key_1>": "<current_value_1>", "<current_key_2>": "<current_value_2>" } }
Alert
Metadata not listed in
nodeTemplate.metadatawill be deleted.Then the node group status will temporarily change to Reconciling: all the nodes in the group will be recreated for the changes to apply.
-
-
Get the public IP address of the node
To connect to a Managed Service for Kubernetes cluster node, specify its public IP address. You can find it using one of the following methods.
- Open the Compute Cloud section in the folder hosting your Managed Service for Kubernetes cluster.
- In the left-hand panel, select
- Click the VM group with the name that matches the Managed Service for Kubernetes node group ID.
- In the window that opens, go to the Virtual machines tab.
- Click the VM whose public address you want to get.
- You will find the public IP address under Network in Public IPv4 address.
-
Find out the ID of the VM group that matches the Managed Service for Kubernetes node group.
The ID is shown in the
INSTANCE GROUP IDcolumn.yc managed-kubernetes node-group listResult:
+----------------------+----------------------+----------------+----------------------+---------------------+---------+------+ | ID | CLUSTER ID | NAME | INSTANCE GROUP ID | CREATED AT | STATUS | SIZE | +----------------------+----------------------+----------------+----------------------+---------------------+---------+------+ | cat684ojo3ir******** | cata9ertn6tc******** | test-nodegroup | cl17i6943n92******** | 2019-04-12 12:38:35 | RUNNING | 2 | +----------------------+----------------------+----------------+----------------------+---------------------+---------+------+ -
View the list of Managed Service for Kubernetes nodes that belong to this group.
The public IP address of the Managed Service for Kubernetes node is shown in the
IPcolumn after~.yc compute instance-group list-instances cl17i6943n92********Result:
+----------------------+---------------------------+--------------------------+---------------+----------------+ | INSTANCE ID | NAME | IP | STATUS | STATUS MESSAGE | +----------------------+---------------------------+--------------------------+---------------+----------------+ | ef31h24k03pg******** | cl17i6943n92********-itif | 10.0.0.27~84.201.145.251 | RUNNING [53m] | | | ef37ddhg9i7j******** | cl17i6943n92********-ovah | 10.0.0.22~84.201.149.184 | RUNNING [53m] | | +----------------------+---------------------------+--------------------------+---------------+----------------+
-
Install kubect
-
Run this command:
kubectl get nodes -o wideResult:
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME cl17i6943n92********-itif Ready <none> 31m v1.13.3 10.0.0.27 84.201.145.251 Ubuntu 18.04.1 LTS 4.15.0-29-generic docker://18.6.2 cl17i6943n92********-ovah Ready <none> 31m v1.13.3 10.0.0.22 84.201.149.184 Ubuntu 18.04.1 LTS 4.15.0-29-generic docker://18.6.2The public IP address is listed in the
EXTERNAL-IPcolumn.
Connect to the node
You can connect to a Managed Service for Kubernetes node over SSH when it is running, i.e., its status is RUNNING. To do this, use ssh in Linux or macOS, or PuTTY
In the terminal, run the following command, specifying the username and public IP address of the node:
ssh <username>@<node_public_IP_address>
If you provided SSH connection credentials when you created the node group using the management console, use the username you specified in the Login field.
If you provided SSH connection credentials when you created the node group using the CLI, Terraform, API, or updated the credentials, use the username you specified in the SSH connection credentials file.
If this is your first time connecting to a Managed Service for Kubernetes node, you may get the unknown host warning:
The authenticity of host '130.193.40.101 (130.193.40.101)' can't be established.
ECDSA key fingerprint is SHA256:PoaSwqxRc8g6iOXtiH7ayGHpSN0MXwUfWHk********.
Are you sure you want to continue connecting (yes/no)?
Type yes into the terminal and press Enter.
In Windows, a connection is established using PuTTY.
- Run Pageant.
- Right-click the Pageant icon in the task bar.
- In the context menu, select Add key.
- Select a PuTTY-generated private key in
.ppkformat. Enter the password for this key, if it is set.
- Run PuTTY.
-
In the Host Name (or IP address) field, enter the public IP address of the VM you want to connect to. Specify port
22and SSH connection type.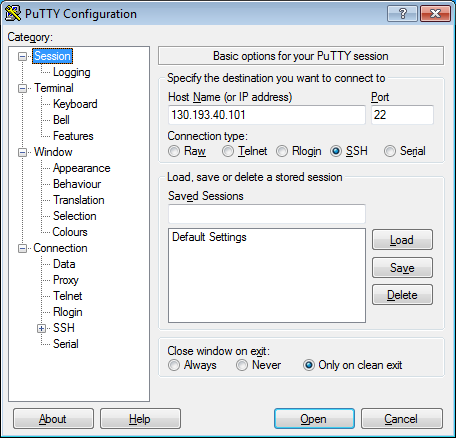
-
In the tree on the left, select Connection - SSH - Auth.
-
Enable Allow agent forwarding.
-
In the Private key file for authentication field, select the private key file.
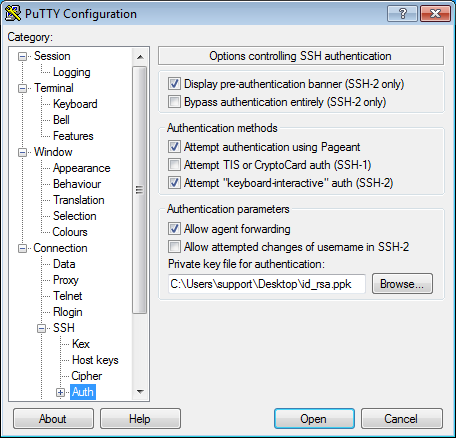
-
Go back to the Sessions menu. In the Saved sessions field, enter any name for the session and click Save. This will save the session settings under the specified name. You can use this session profile to connect with Pageant.
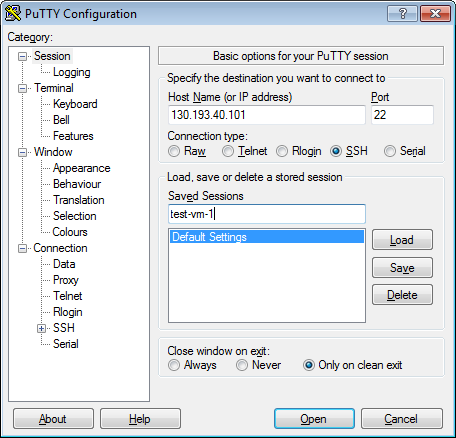
-
Click Open. If this is your first time connecting to the Managed Service for Kubernetes node, you may get the unknown host warning:
Click Yes. This will open a terminal window prompting you to enter the username to use for connection.
Enter the username:
- If you provided SSH connection credentials when you created the node group using the management console, enter the username you specified in the Login field.
- If you provided SSH connection credentials when you created the node group using the CLI, Terraform, API, or updated the credentials, enter the username that you specified in the SSH connection credentials file.
Press Enter. If everything is configured correctly, a connection to the server will be established.
-
If you saved the session profile in PuTTY, you can use Pageant for future connections:
- Right-click the Pageant icon in the task bar.
- Select Saved sessions.
- In the saved sessions list, select the session you need.