
Yandex Key Management Service
Yandex Key Management Service
A service for managing cryptographic keys. Use keys to protect the secrets, personal data, and sensitive information you store in the cloud.
Key management
Create and delete keys, set up access policies, and perform rotation via the management console, CLI, or API.
Data encryption
Yandex KMS implements symmetric and asymmetric cryptography. Use the REST or rpc API to encrypt and decrypt small amounts of data, such as secrets and local encryption keys, as well as to sign data using e-signature schemes.
Access control and security
You manage access to encrypted data, and Yandex KMS ensures the reliability and physical security of keys. Hardware Security Modules (HSMs) are available.
SDK integration
Encrypt small amounts of data using the SDK in Java or Go. To encrypt larger amounts of data, the service is integrated with popular encryption libraries, including the AWS Encryption SDK and Google Tink.
Audit key actions
Verify access to encrypted data via key logs. Yandex KMS registers all API requests, including actions for managing keys and using keys to encrypt and decrypt data.
Integration with other services
Integration with Yandex Lockbox makes it possible to encrypt secrets with your own keys. Secrets and data can also be protected using encryption keys in Managed Service for Kubernetes.
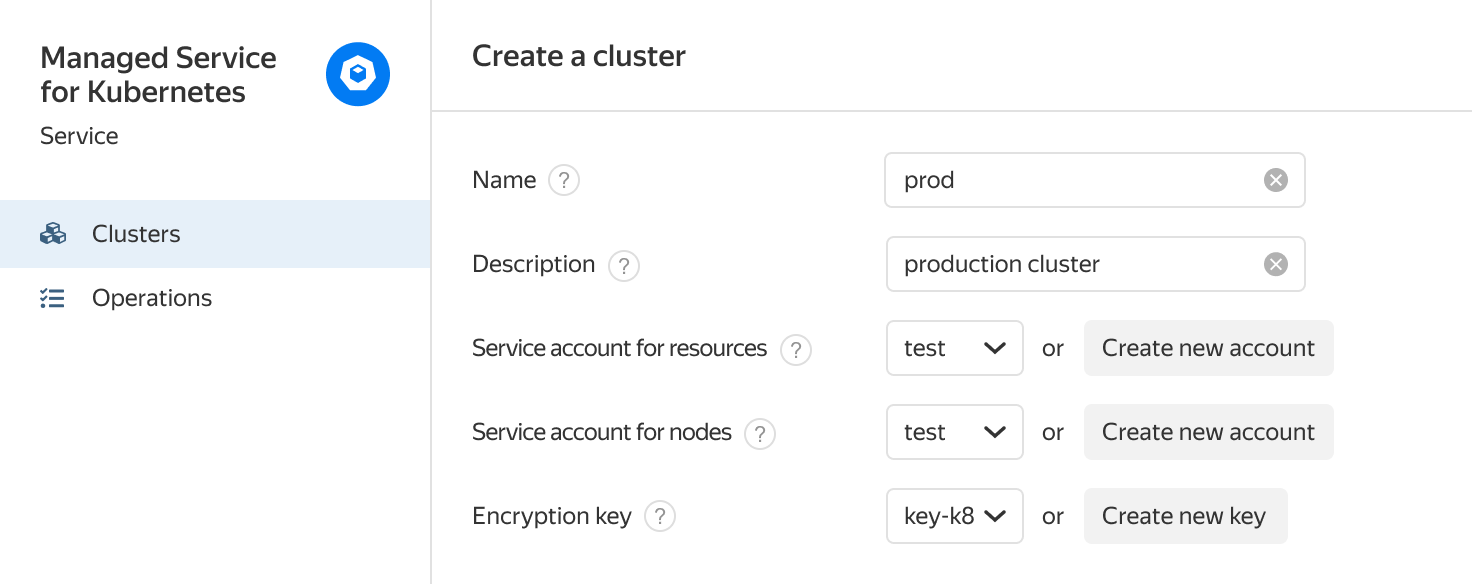
Getting started
Encrypt your secrets with Yandex Managed Service for Kubernetes using a KMS key. To do this, create a KMS key and use it when creating a Kubernetes cluster.
Questions and answers
A key is a set of versions, each of which defines an algorithm and cryptographic material for data encryption or decryption operations. The key is created along with its first version, which becomes the primary one. It’s used by default in key operations unless you specify a different version in the input parameters.