Envelope encryption
Encryption with the encrypt method has a limit on the maximum size of data to encrypt (32 KB). Larger data volumes cause a number of problems:
-
Increased load on KMS caused by encryption and decryption operations.
-
Reduced encryption and decryption performance if using the encrypt and decrypt methods with larger encryption data volumes.
The encrypt and decrypt operation time includes transferring data from the client to KMS and back. As the amount of encrypted data increases, its transmission time and the load on the network increase, too.
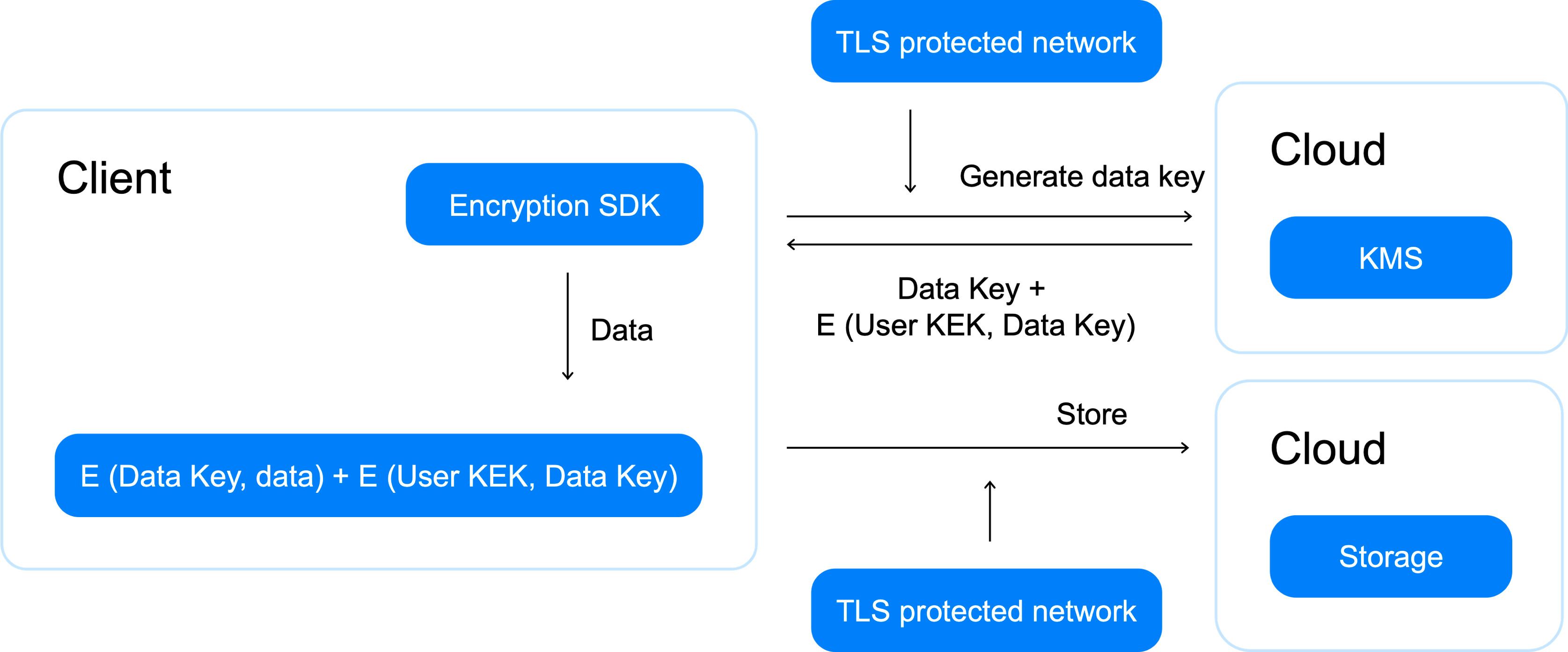
Envelope encryption is mainly implemented on the client side and helps avoid the problems listed above.
Description of the encryption process
Unlike direct
encryption, where a KMS key acts as a data encryption key, envelope encryption involves two types of keys:
- Data encryption key (DEK).
- Key encryption key (KEK).
Encryption is preformed as follows:
-
The client generates a DEK and locally encrypts data with it.
To generate a high-entropy key, we recommend using the generateDataKey. It generates keys based on the Fortuna algorithm that collects entropy from various sources (RDSEED and RDRAND, /dev/urandom, host entropy).
-
The client sends an encrypt request to KMS for DEK encryption.
-
In response, the client receives the encrypted DEK.
In this scheme, the KMS key that the DEK is encrypted with acts as a KEK.
-
The unencrypted DEK is destroyed by the client.
-
The encrypted DEK is saved by the client along with the ciphertext.
When using envelope encryption, a wider set of algorithms is available for local encryption. You can also encrypt data with multiple DEKs, for example, to enable random access to ciphertext.
Decryption process description
Decryption is performed as follows:
- The client reads the encrypted DEK stored along with the encrypted data.
- The client sends a decrypt request to KMS for DEK decryption.
- In response, the client receives the decrypted DEK.
- The encrypted data is locally decrypted using the DEK.
- The DEK is destroyed.
Implementation features of envelope encryption
Envelope encryption shifts some of the responsibility for secure data encryption to the client. When implementing this scheme, it is important to:
-
Use secure algorithms for local encryption.
-
Make sure not to save DEKs as plaintext.
Warning
A plaintext DEK should only be decrypted for the duration of data encryption or decryption operations and destroyed immediately afterwards.
-
Use different DEKs for different data.
-
Generate new DEKs when data is re-encrypted.
To avoid errors, we recommend using the AWS Encryption SDK or Google Tink for client-side encryption.