Uploading logs from Yandex Audit Trails
Audit Trails helps you collect and export audit logs as well as apply the analysis and rapid response tools to events at the Yandex Cloud resources level. OpenSearch acts as a SIEM system to analyze logs and respond to security events.
You will learn how to set up the export of logs from Audit Trails in just a few steps using Yandex Data Streams and Yandex Data Transfer, with Yandex Managed Service for OpenSearch as a SIEM system to analyze logs and respond to security events.
Create a trail to upload audit logs for Yandex Cloud resources to a Yandex Data Streams data stream. Once done, configure continuous log delivery to a Yandex Managed Service for OpenSearch cluster using Yandex Data Transfer.
You can export organization, cloud, or folder logs.
To export audit logs:
- Get your cloud ready.
- Create a trail to send logs to the stream in Data Streams.
- Create a Managed Service for OpenSearch cluster.
- Set up a transfer to deliver logs to the Managed Service for OpenSearch cluster.
- Check the result.
- Upload additional content.
If you no longer need the resources you created, delete them.
Getting started
Sign up for Yandex Cloud and create a billing account:
- Navigate to the management console
- On the Yandex Cloud Billing
ACTIVEorTRIAL_ACTIVEstatus. If you do not have a billing account, create one and link a cloud to it.
If you have an active billing account, you can navigate to the cloud page
Learn more about clouds and folders here.
Required paid resources
-
Managed Service for OpenSearch cluster: Use of computing resources and storage size (see Managed Service for OpenSearch pricing).
-
Public IP addresses if public access is enabled for cluster hosts (see Virtual Private Cloud pricing).
-
Data Streams (see Data Streams pricing). The cost depends on the pricing model:
- Based on allocated resources: You pay a fixed hourly rate for the established throughput limit and message retention period, and additionally for the number of units of actually written data.
- On-demand: You pay for the performed read/write operations, the amount of read or written data, and the actual storage used for messages that are still within their retention period.
-
Managed Service for YDB database, operating in serverless mode: data operations, amount of stored data and backups (see Managed Service for YDB pricing).
Create a trail to send logs to a Data Streams data stream
Create a trail to send logs to a data stream named audit‑trails. Using a stream with this name makes it easier to upload the Security Content library objects.
When creating a trail, select the log collection scope.
Create a Managed Service for OpenSearch cluster
Create a Managed Service for OpenSearch cluster with any suitable configuration.
-
If you do not have Terraform yet, install it.
-
Get the authentication credentials. You can add them to environment variables or specify them later in the provider configuration file.
-
Configure and initialize a provider. There is no need to create a provider configuration file manually, you can download it
-
Place the configuration file in a separate working directory and specify the parameter values. If you did not add the authentication credentials to environment variables, specify them in the configuration file.
-
Download the trails-to-opensearch.tf
This file describes:
- Network.
- Subnet.
- Security group and rules required to connect to a Managed Service for OpenSearch cluster.
- Managed Service for OpenSearch target cluster.
- Transfer.
-
In the
trails-to-opensearch.tffile, specify the following variables:os_version: OpenSearch version in the target cluster.os_admin_password:adminuser password.transfer_enabled: Set to0to ensure that no transfer is created until you create endpoints manually.
-
Validate your Terraform configuration files using this command:
terraform validateTerraform will display any configuration errors detected in your files.
-
Create the required infrastructure:
-
Run this command to view the planned changes:
terraform planIf you described the configuration correctly, the terminal will display a list of the resources to update and their parameters. This is a verification step that does not apply changes to your resources.
-
If everything looks correct, apply the changes:
-
Run this command:
terraform apply -
Confirm updating the resources.
-
Wait for the operation to complete.
-
All the required resources will be created in the specified folder. You can check resource availability and their settings in the management console
-
Set up a transfer to deliver logs to the Managed Service for OpenSearch cluster
-
-
Database type:
Yandex Data Streams. -
Endpoint settings:
-
Connection settings:
- Database: Select the Managed Service for YDB database from the list.
- Stream: Specify the name of the stream in Data Streams.
- Service account: Select or create a service account with the
yds.editorrole.
-
Advanced settings:
- Conversion rules:
AuditTrails.v1 parser.
- Conversion rules:
-
-
-
-
Database type:
OpenSearch. -
Endpoint parameters:
-
Connection:
-
Connection type:
Managed Service for OpenSearch cluster.- Managed Service for OpenSearch cluster: Select the source cluster from the list.
-
User and Password: Enter the name and password of the user who has access to the database, e.g.,
adminuser.
-
-
-
-
Create and activate your transfer:
ManuallyUsing Terraform- Create a Replication-type transfer configured to use the new endpoints.
- Activate the transfer and wait for its status to change to Replicating.
-
In the
trails-to-opensearch.tffile, specify these variables:source_endpoint_id: Source endpoint ID.target_endpoint_id: Target endpoint ID.transfer_enabled:1to create a transfer.
-
Validate your Terraform configuration files using this command:
terraform validateTerraform will display any configuration errors detected in your files.
-
Create the required infrastructure:
-
Run this command to view the planned changes:
terraform planIf you described the configuration correctly, the terminal will display a list of the resources to update and their parameters. This is a verification step that does not apply changes to your resources.
-
If everything looks correct, apply the changes:
-
Run this command:
terraform apply -
Confirm updating the resources.
-
Wait for the operation to complete.
-
-
-
The transfer will be activated automatically. Wait for its status to change to Replicating.
Check the result
Make sure the data from Audit Trails is successfully uploaded to OpenSearch:
-
Wait for the transfer status to change to Replicating.
-
Connect to the target cluster using OpenSearch Dashboards.
-
Select the
Globaltenant. -
Create a new index template named
audit-trails*:- Open the management panel by clicking
- Under Management, select Stack Management.
- Go to Index Patterns and click create an index pattern at the bottom of the page.
- In the Index pattern name field, specify
audit-trails*and click Next step. - In Time field, select
application_usage_daily.timestampand click Create index pattern.
- Open the management panel by clicking
-
Open the management panel by clicking
-
Under OpenSearch Dashboards, select Discover.
-
The dashboard that opens should contain data from Audit Trails in Elastic Common Schema
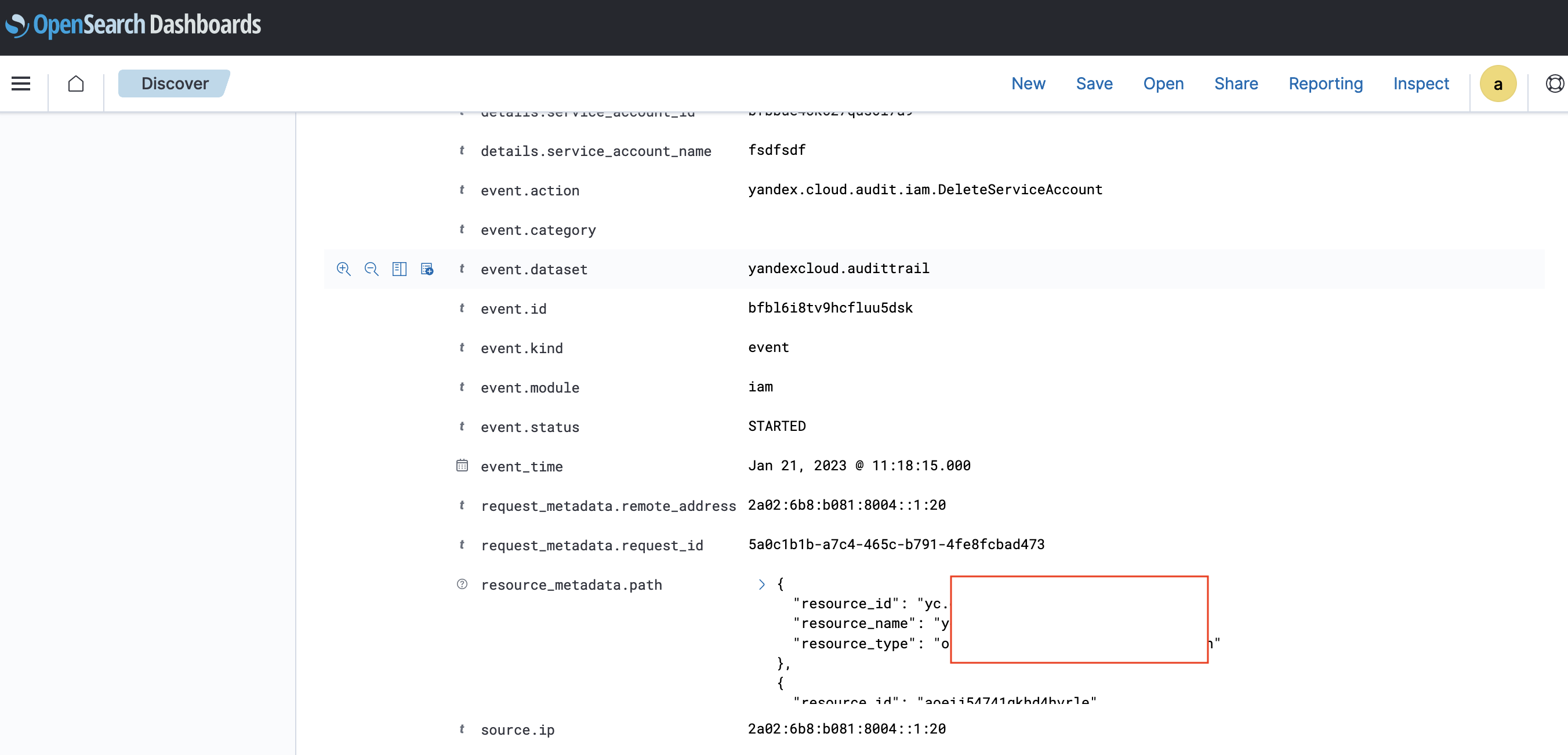
Warning
Data delivery to Managed Service for OpenSearch target adheres to the at least once mode: if the tables being transferred do not have a primary key, duplicate entries can be created in the audit logs.
Upload additional content
For your convenience, the Yandex Cloud security team created Solution Library with examples and recommendations for building a secure infrastructure in Yandex Cloud. The library is available in this public GitHub repository
- Dashboard with use cases and statistics.
- Set of ready-to-use queries to search for security events.
- Sample events with preset alerts (the client should specify the alert destination on their own).
All required event fields are converted to Elastic Common Schema (ECS)
To use Security Content:
-
Clone the Yandex Cloud Security Solution Library repository:
git clone https://github.com/yandex-cloud-examples/yc-export-auditlogs-to-opensearch.git -
Connect to the target cluster using OpenSearch Dashboards.
-
Open the management panel by clicking
-
Under Management, select Stack Management.
-
Go to Saved Objects and import files from the
yc-export-auditlogs-to-opensearch/update-opensearch-scheme/content-for-transfer/folder:dashboard.ndjsonfilters.ndjsonsearch.ndjson
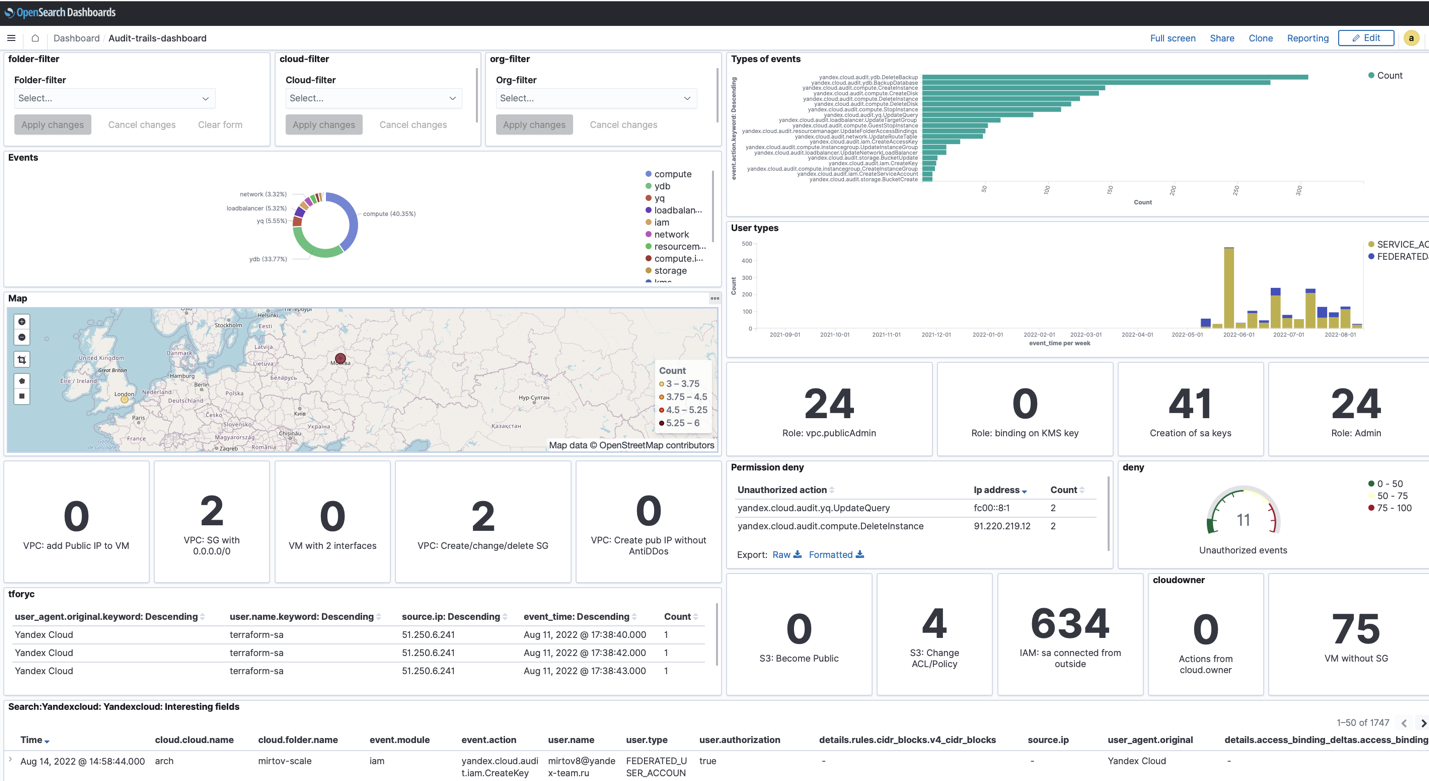
Dashboard
Use the ready-made Audit-trails-dashboard:
- Open the management panel by clicking
- Under OpenSearch Dashboards, select Dashboard.
- Select
Audit-trails-dashboardin the dashboard list.
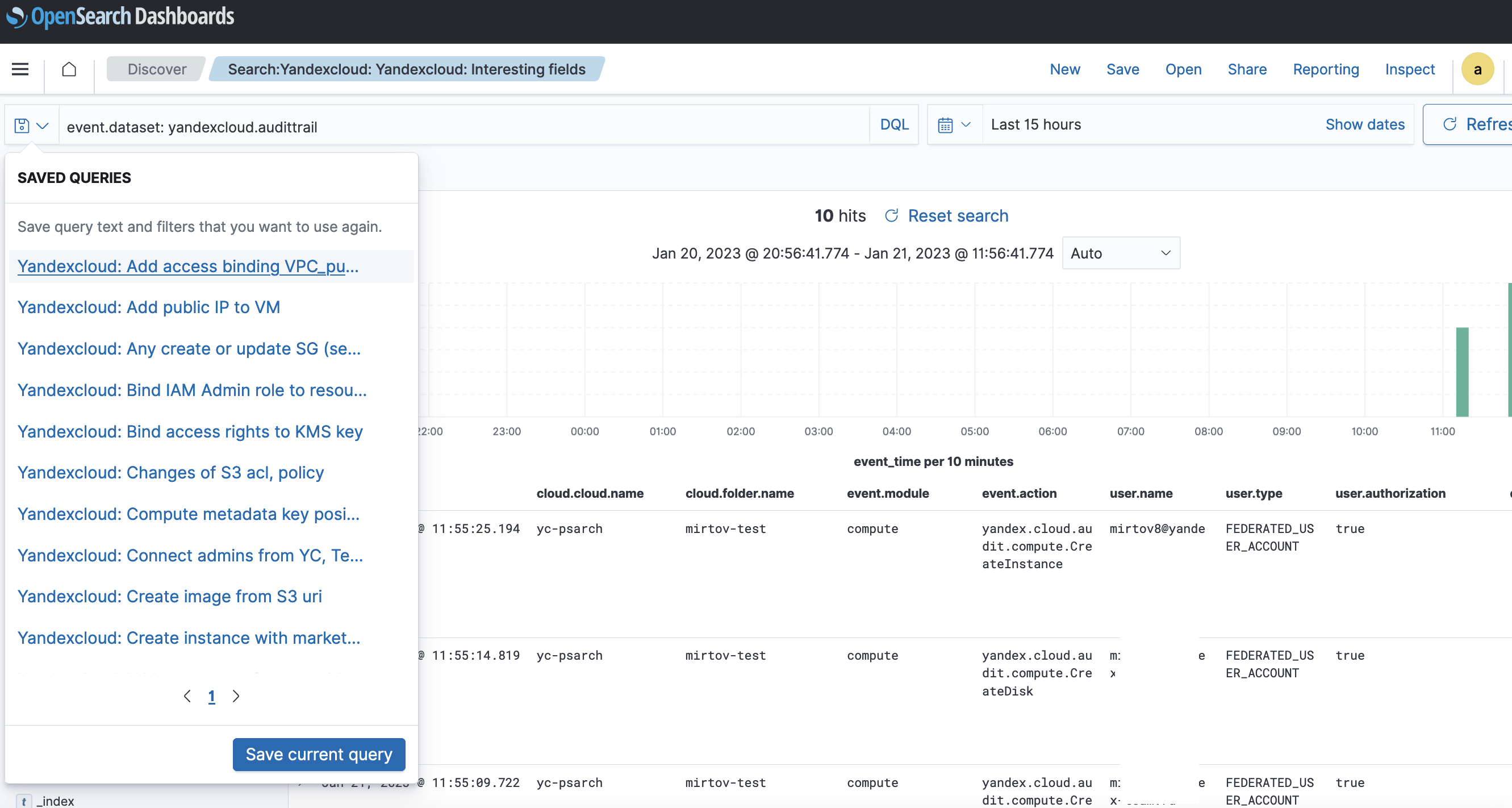
Security events
Run a ready-to-use query to view security events that can be selected using filters.
- Open the management panel by clicking
- Under OpenSearch Dashboards, select Discover.
- In the Open tab, select
Search:Yandexcloud: Yandexcloud: Interesting fields.
Setting up alerts
Use code examples for the monitor and trigger entities when setting up alerts
-
Open the management panel by clicking
-
Under OpenSearch Plugins, select Alerting.
-
Copy the sample file contents and paste them into the creation window:
Delete the resources you created
Note
Before deleting the resources, deactivate the transfer.
To reduce the consumption of resources you do not need, delete them:
-
Delete the Managed Service for YDB database.
-
Delete the Audit Trails trail.
-
Delete other resources using the same method used for their creation:
ManuallyUsing Terraform-
In the terminal window, go to the directory containing the infrastructure plan.
Warning
Make sure the directory has no Terraform manifests with the resources you want to keep. Terraform deletes all resources that were created using the manifests in the current directory.
-
Delete resources:
-
Run this command:
terraform destroy -
Confirm deleting the resources and wait for the operation to complete.
All the resources described in the Terraform manifests will be deleted.
-
-